User authentication is a key concern for any modern web project. Not just web but authentication is used in almost every sector such as banking, governments, and many others. For the purpose of user authentication in web or mobile apps two main ways which are Session and Tokens. In this explanatory article, we discuss session vs token authentication necessity and mechanism.
Authentication is the process of verifying whether the user who they claim they are. Let’s consider a simple example of ABC Bank, before fully digging into session vs authentication chapter.

In the initial stage, a user is presented with the login screen as shown on the left side of the image. As the user enters the login credentials, the request is handled by the backend service and validates with the database or cloud server.
The authenticity of the login credentials are checked and the response is sent to the user by the backend. If the user is valid, a success request is sent and the user can access the services provided otherwise the authentication is not granted and the user cannot access the system.
As the access is granted a session is created in the database along with the login event and provides the session-id in form of a cookie.
Session – what is it?
The session can be defined as the way or method of authenticating a user without them having to type the username and password every time they need to access the system which requires authenticity.
The process begins with the user filling out their login credentials and submitting it to the server. The server validates and creates a session on the database and then responds with a session-id. The session-id is stored in the browser as cookies which will be sent back to the server on each subsequent request.
Then the server responds with the context that is authentic for the currently signed-in user. A stateful session is in between the client, backend, and the server.
Session-Based Authentication flow
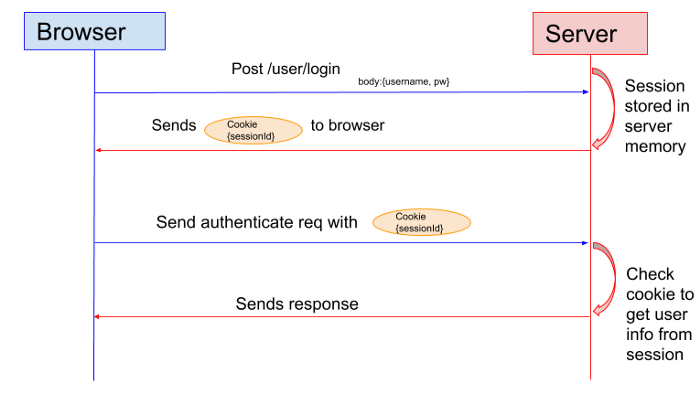
Example of Session Management
Let’s take the example of Facebook. Initially, we need to type in our username and password to get into the website or mobile app to confirm that we are the owner of the account.
If there would be no service of session management, image how annoying it would be typing in username and password for every little thing such as uploading a picture, comments, likes, and so on. This would be necessary if there was no session management system because Facebook wants to confirm that you are the account owner before doing those little things.
With the presence of session-id, Facebook knows the account belongs to us and thus lets us perform those operations without that login stuff.
Drawbacks of session-based authentication
- Every authentication server creates a new session and stores it into the server. With the presence of an excessive number of users, it creates a heavy load onto the server.
- As the session gets stored in the server memory, it creates a problem with scalability.
- Vulnerable to CSRF (Cross-site request forgery) attack.
Token – what is it?
Token-based authentication is one of the better ways of authentications for secure and safe user verification. As the user enters the login credentials, the server creates a Token (JSON Web Token) which is created by the private key on the server.
As the Token is created from the server it is passed back to the browser and is stored in the local storage which reduces the load on the server. Whenever the server requests authentication, JWT is added to the authorization header prefix.
The signed header is used for validation upon server requests. Then the server only needs to validate the signature with the header. This is more robust when dealing with a distributed system in the cloud.
Token-Based Authentication flow
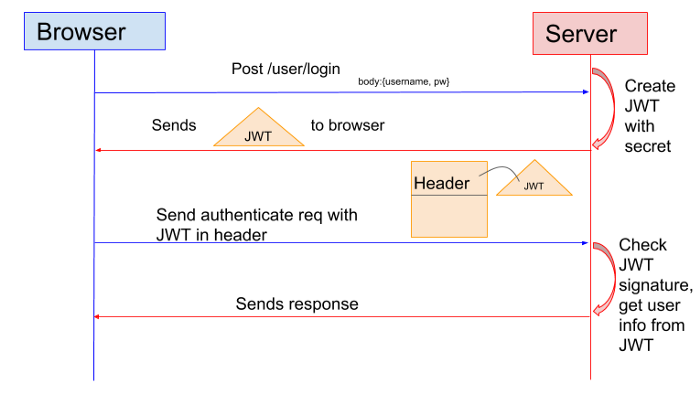
Pros of Token-Based Authentication
- Tokens contain all the necessary information that is necessary for the validation. From a scalability point of view, it is great as it doesn’t load the server and no verification needs to be stored on the server.
- Less risk of CSRF (Cross-site request forgery) attack.
- We can easily transfer information between parties in a more convenient and more secure manner.
A basic example of JSON Web Token

JWT encoded value is presented on the left side of the image. The encoded value consists of various components like header, payload, and verify the signature. With the use of payload, we can provide various information regarding the user regarding their roles and accessibility.
With a modern programming framework it becomes more efficient and more secure working with JSON Web Token.
Conclusion
As compared to session-based authentication, token-based authentication is much better and efficient to work with. Regarding core aspects like scalability, security, server load token-based authentication is more promising than session-based authentication.
In this comparison of token vs session based authentication, it maybe a developer’s preference but the wider and future scaling of application need might help you understand what to adopt at an early application development stage.
What’s your thought? Let’s discuss.


From the article it appears there is no difference between session and token.